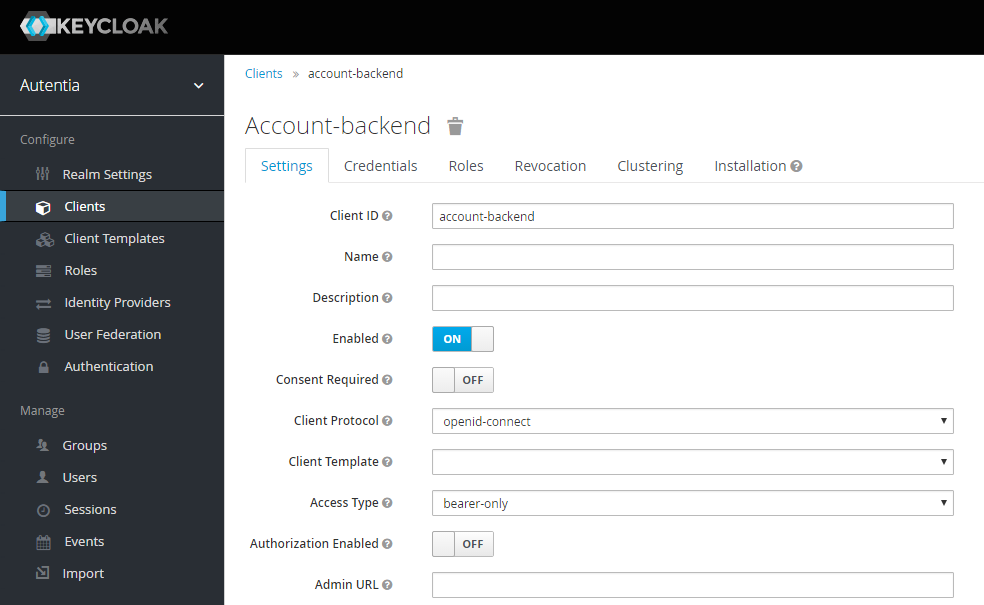
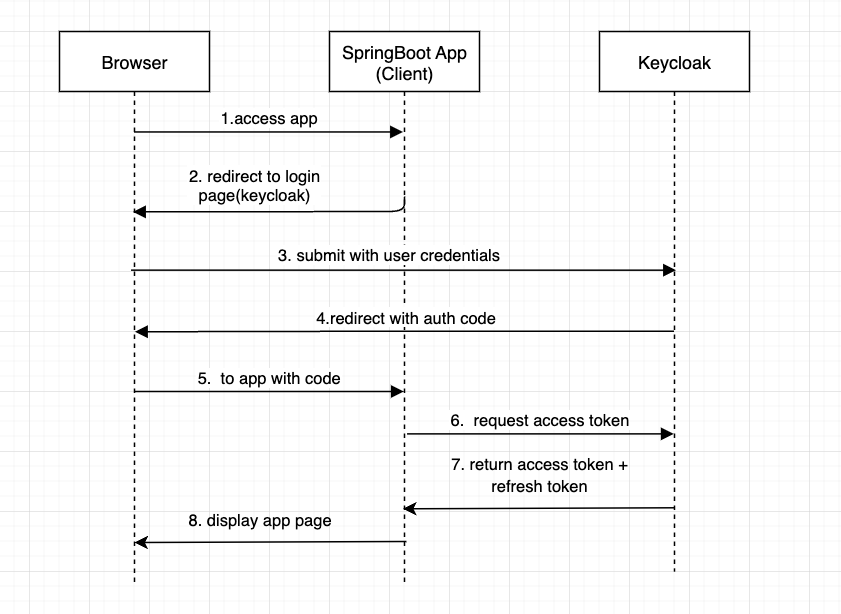
Part 6 - How To Secure Distributed Apps with KEYCLOAK - Micro Service Rest API Bearer Only case - YouTube
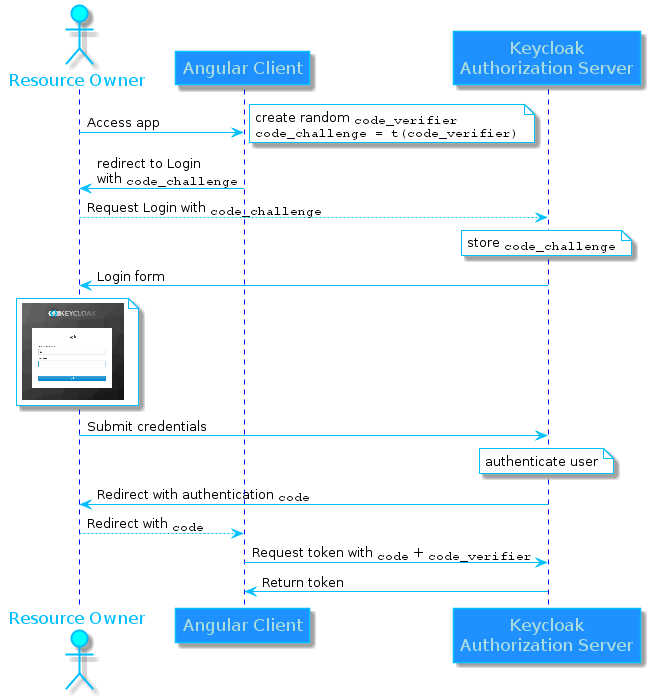
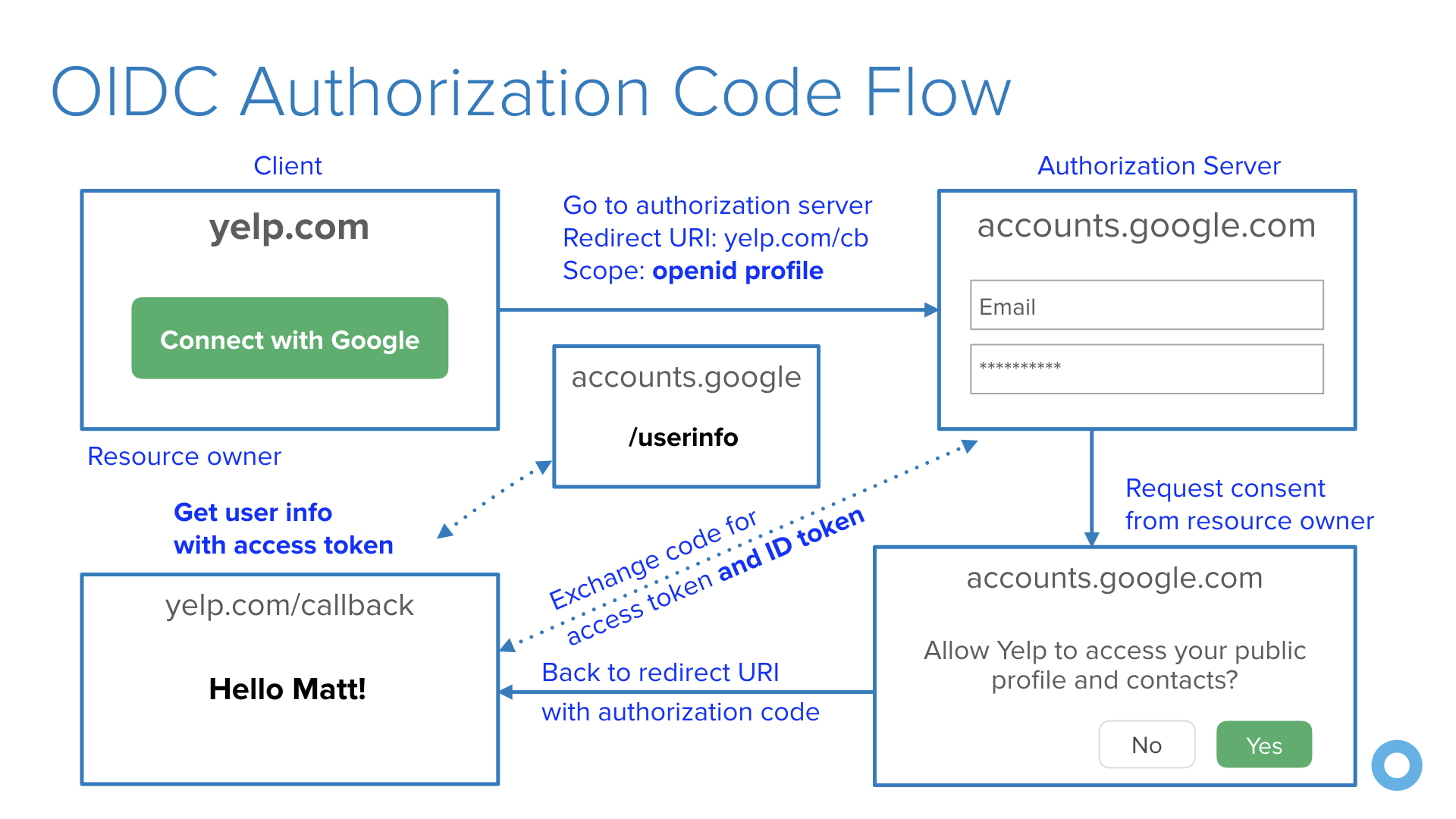
Securing Web Applications With Keycloak Using OAuth 2.0 Authorization Code Flow and PKCE - Jeroen Meys — Ordina JWorks Tech Blog
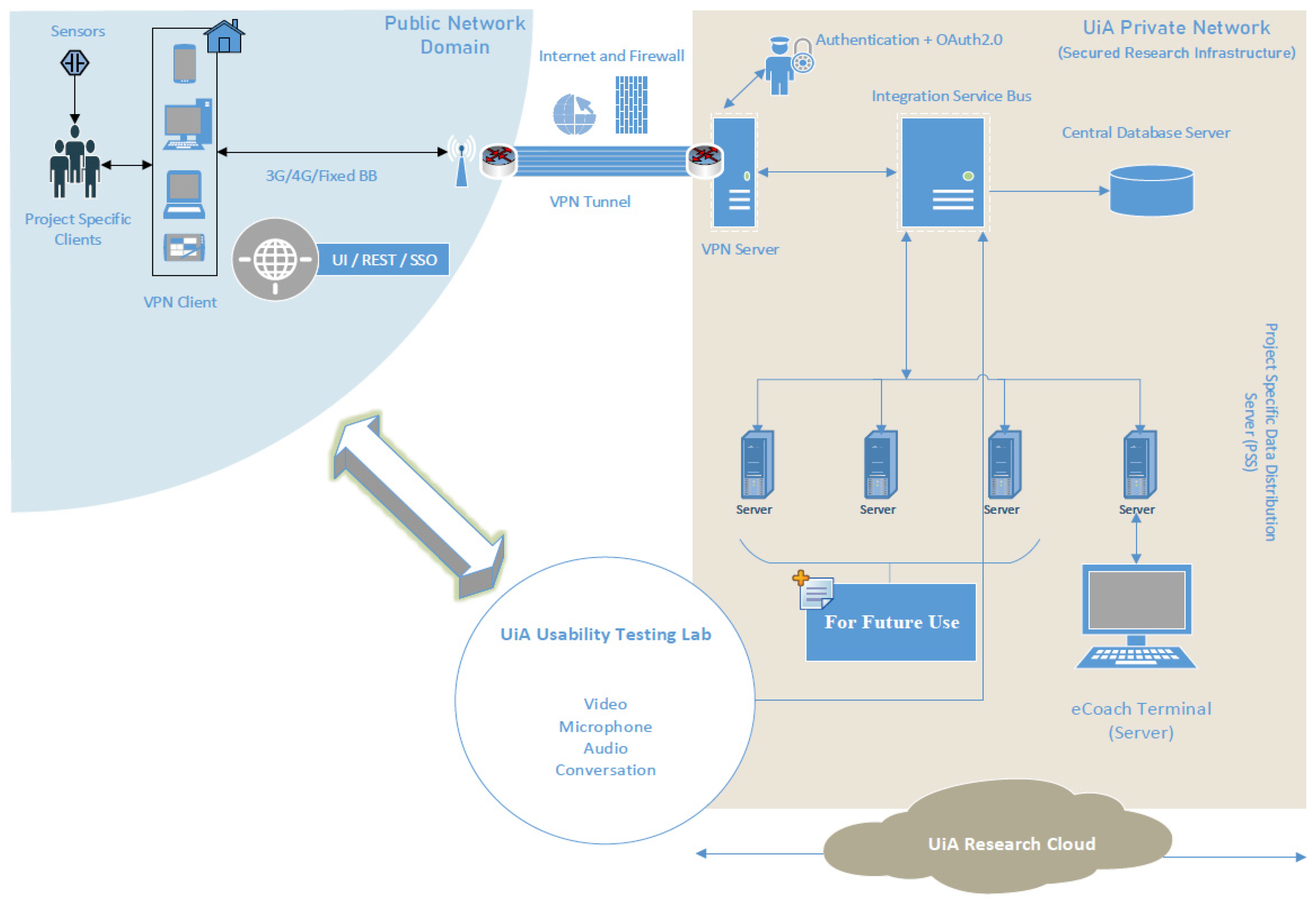
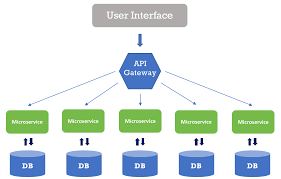
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study